Today’s Cybersecurity Dilemma: Analyzing over 100,000 security incidents daily from more than 150 distinct threat actors
The Challenges:
- Security teams struggle to keep up with threats
- Uncertainty about relevant and significant threats
- Blind spots from ineffective, scattered cybersecurity tools

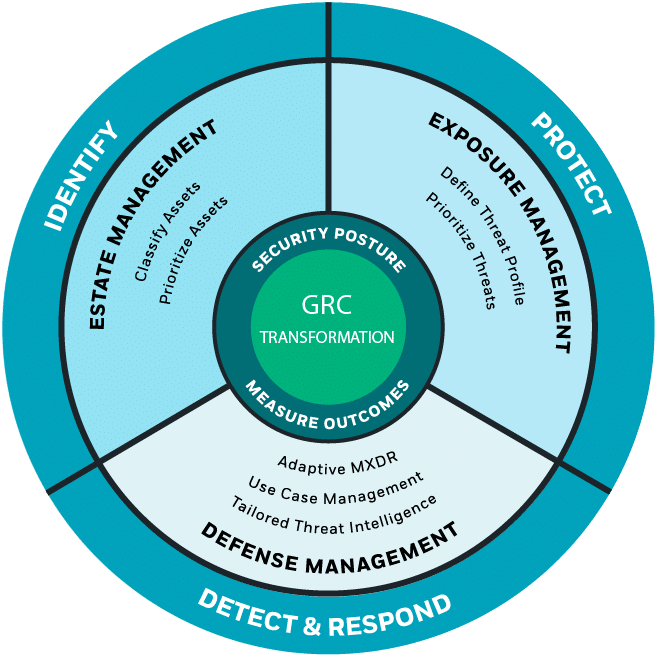
The Solution: Defend Against the Threats That Matter Most
CyberProof provides an integrated threat-led platform that combines:
- Estate (Asset) Management: Tag, classify, and prioritize known and unknown assets to understand your exposure – continuously
- Exposure Management: Focus on relevant threats using CTEM and ASCA frameworks – continuously
- Defense Management: Optimize detection and response playbooks – continuously
- Resulting in GRC Transformation: Mitigate Global Risk, Define Business Outcomes & ROI, Mature Security Posture
SecOps & Risk Mitigation
CyberProof uses OSINT and threat intelligence feeds for visibility into threats.
CyberProof’s adaptable playbooks address continuously evolving threats with updated strategies.
Professionals manage sophisticated networks, leveraging experience to counter advanced threats.
Professionals manage sophisticated networks, leveraging experience to counter advanced threats.
24/7 global SOC support ensures incident response with guaranteed SLA.
24/7 global SOC support ensures incident response with guaranteed SLA.
CyberProof develops recovery plans, restoring capabilities after a cyber incident.
Classify and manage enterprise assets, understanding risks and data sensitivity.
Non-destructive tests uncover potential exploits in assets and applications.
Mitigate security issues early with CyberProof’s training and awareness programs.
Rigorous security assessment for on-premise and cloud applications to ensure protection.
IAM manages user access, monitors for anomalies, ensuring security.
Cloud First approach ensures compliance and security within cloud environments.
Managed service for SIEM, EDR, MXDR, and threat intelligence solutions.
Identify, assess, and mitigate security vulnerabilities through regular scanning.
Partners
“Today I have complete visibility into the entire environment, in real time”
Jamil Farshchi | Equifax CISO
CyberProof CTEM
CyberProof’s CTEM platform, powered by Interpres, is able to continuously identify, assess, and prioritize risk, while enhancing defense services like MDR, Vulnerability Management and Use Case Management to address evolving threats. Take proactive steps to fortify your security today!
Threat Alerts
North Korean Threat Actors Deploy PylangGhost RAT variant
A North Korean-aligned threat actor group has developed a new Python-based remote access trojan called “PylangGhost,” representing a significant evolution in their attack capabilities. This malware shares functional similarities with the previously documented GolangGhost RAT and specifically targets employees with cryptocurrency and blockchain experience through sophisticated social engineering campaigns. The attacks primarily affect users in India, though the scope remains limited based on current intelligence, and demonstrate the threat actors’ continued focus on financial gain through both credential theft and fraudulent employment schemes.
The attack chain begins with fake job recruitment websites impersonating legitimate companies in the cryptocurrency sector, where victims are lured through skill-testing pages that eventually request camera access for video interviews. When users attempt to enable their cameras, they receive instructions to copy and paste malicious commands that allegedly install necessary video drivers. These commands download ZIP files containing the PylangGhost modules along with Visual Basic scripts that extract and execute the Python-based trojan. The malware establishes persistence through registry modifications and communicates with command and control servers using RC4 encryption over HTTP.
PylangGhost consists of six well-structured Python modules that mirror the functionality of its Golang counterpart, supporting commands for system information gathering, file operations, remote shell access, and extensive browser credential theft from over 80 extensions including cryptocurrency wallets and password managers. The threat actors deploy different variants based on the target’s operating system, using the Python version for Windows systems while maintaining the Golang variant for macOS users, with Linux systems currently excluded from these campaigns.
New Amatera Stealer Raises the Bar for Info Stealers
A new malware-as-a-service offering known as Amatera Stealer has recently emerged, positioning itself as a more advanced evolution of the earlier ACR Stealer. Priced up to $1,499 annually, the tool enables a wide range of threat actors to steal sensitive data from victims, including browser credentials, messaging app content, and password manager entries. Its rising popularity and technical sophistication make it a growing concern across multiple sectors.
Amatera is distributed through ClearFake web injection campaigns, in which legitimate websites are compromised to display fake CAPTCHA prompts. Victims are socially engineered to run a malicious command using a technique called ClickFix, which tricks them into opening a system dialog and pasting in attacker-supplied code. This launches a multi-stage infection process that uses obfuscation techniques, bypasses built-in security like AMSI (Anti-Malware Scan Interface), and injects malware into legitimate system processes. It also uses EtherHiding, a tactic where malicious code is hidden inside blockchain smart contracts to avoid detection.
Technically, Amatera is built to evade modern security tools. It uses NTSockets, a low-level communication method that avoids standard Windows networking libraries, making its traffic harder to detect. It also relies on WoW64 syscalls, a way to execute system-level code while bypassing user-mode monitoring. For command-and-control, it connects through Cloudflare infrastructure using spoofed headers that make its traffic appear legitimate. These evasion strategies, combined with its broad data theft capabilities and ability to deploy additional malware, make Amatera one of the most capable info-stealers currently in circulation.